
Pragmatic approach to assess the security of an organisation
Pragmatic approach to assess the security of an organisation
For years I’ve been helping organisations get the best out of their people, processes and technologies. This has also enabled me to learn and evolve on both professional and personal level.
This article is aimed at 2 types of IT people :
- Those who wear multiple hats in their IT department including being responsible for Cybersecurity
- Those who come from a technical cybersecurity background, currently working in a more leadership role.
In the last few years, I’ve been to countless meetings, seminars, open houses and security summits where a large number of the businesses and IT leaders from various organisations expressed similar concerns regarding the security posture of their organisation. They generally have a random approach to improve their security posture which is fine when you don’t have dedicated security staff. At least something is better than nothing! However a more thought after and pragmatic approach is the one that’ll provide better and more effective results.
During such gatherings, I was mostly asked this fundamental question-
” Where to start?”

Those conversations prompted me to present in one such seminar a pragmatic approach based on my real life experiences in the trenches. Here I’m sharing my high-level strategy which I believe would benefit organisations that want to improve their security posture but don’t have the budget to hire a CISO or dedicated security staff or for similar reasons.
Before starting with the main topic, I want to make one point very clear that the success of your security programme heavily depends on one thing and that is top-management buy-in. I can’t stress enough how important it is to have full support and governance from the top.
As security professionals, our job is to act as evangelists to transform the mentality and culture of our organisation. However, to become the change its imperative to understand the culture of the organisation and adjust accordingly. I learnt this lesson years ago when I joined an organisation with the mind set of changing their culture and guess what happened? I got frustrated and decided to move on. Since then, I’ve changed my strategy and started to understand the culture first and then adjust my objectives to help organisations in achieving their business objectives. A win-win situation for everyone.
As security leaders, sometimes we have to use different tactics in different situations to convince the audience or our organisation/business that security is a business enabler, not a blocker. But that itself can be a tough job! However, if you catch the culture earlier and then develop your security strategic objectives which are aligned with the business objectives, you have a better chance to make a difference.

Now coming back to our main topic, where to start? Once you get the green light from top management, it’s time to create a high-level strategy and find the right approach to start the programme as there is no one fit for all. There are different frameworks available which can be used, e.g. COBIT, SABSA, NIST. However, I use these frameworks as a guide to follow the industry best practices and use my experiences to create a strategy on how to kick off the programme. In my opinion, we should treat this initially as a project. Once you achieve the objectives set out in the project, this should become a part of the continuous improvement process. In Cybersecurity, there’s no such thing as a “perfect security posture”. As technologies change quite rapidly so do the nature of attacks. Its a continuous improvement process!
There are two phases in assessment of overall security of the environment:
Phase 1: Understand the organisational goals and other contexts.
In this phase, you will be spending a lot of your time interviewing (meeting) people of your organisation, reviewing processes and technologies. E.g. stakeholders, workforce, regulations, culture, partners, customers, competitors, organisation’s objectives and risk appetite. The aim is to gather as much information as you possibly can, so you can analyse the data and get a clear understanding of who and what you are dealing with. Clarity breeds mastery!
You can run the 2nd phase in parallel to speed up the process
Phase 2: Conduct security assessment (Health Check) on your environment
I use 5 step process to get a holistic view of the organisation’s current threats and risks.
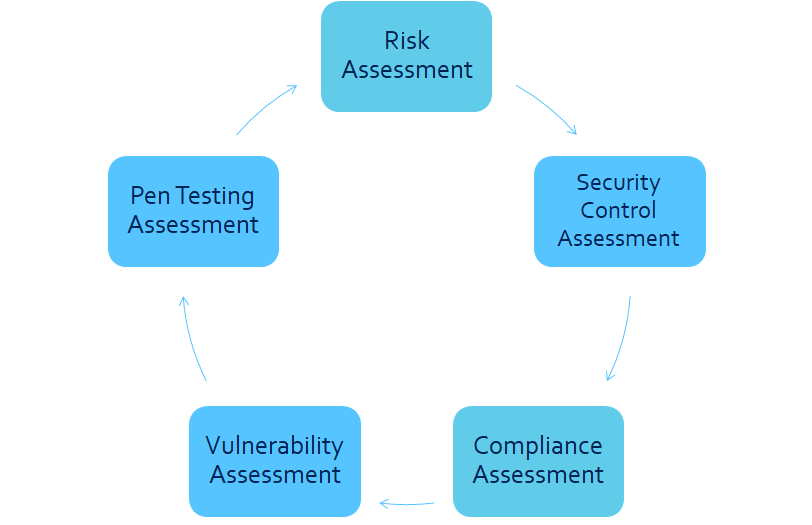
Each step has a different technique and methodology to complete the assessment. Combining the result of all these assessments will give you a complete picture of your current security estate and risks. To know more about each of these assessments, please go to our services section or contact us to speak to one of consultant.
As always thank you for the gift of your time to read my blog.!
0 Comments
Request A Free Quote!

